Agent diary
Each agent maintains a diary — a high-level record of activities and internal reasoning.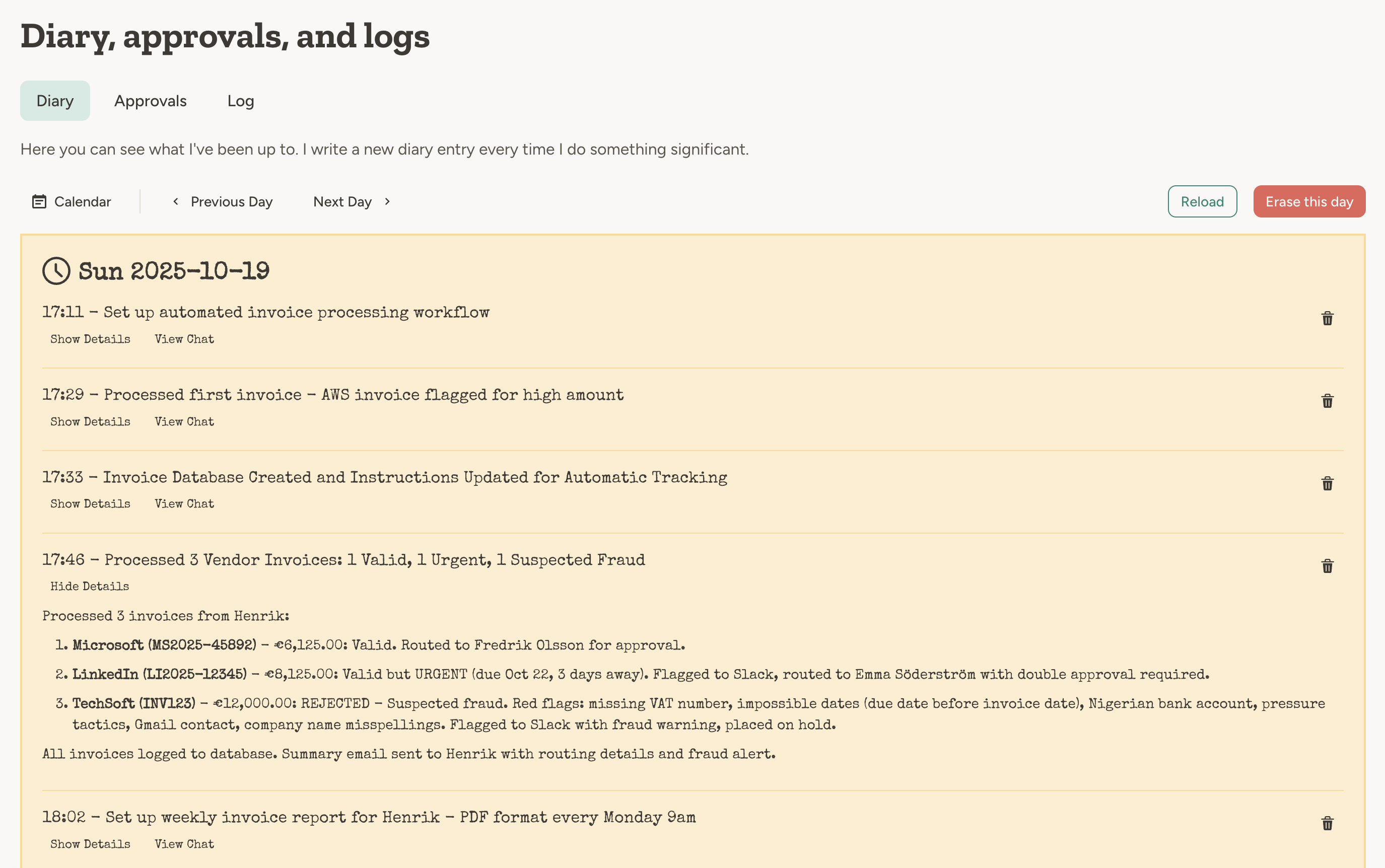
- It has processed a trigger (email, scheduled task, webhook, etc).
- It has done something significant in the chat.
In the chat, the agent decides when to write a diary entry based on the conversation content. This differs from handling triggers and events, where the agent will always write a diary entry. Writing a diary entry after every chat message would be too verbose and not useful.
Activity log
The activity log is a live-updated technical log of all triggers that the agent has processed. Triggers could be for example an email, a scheduled task, or a webhook.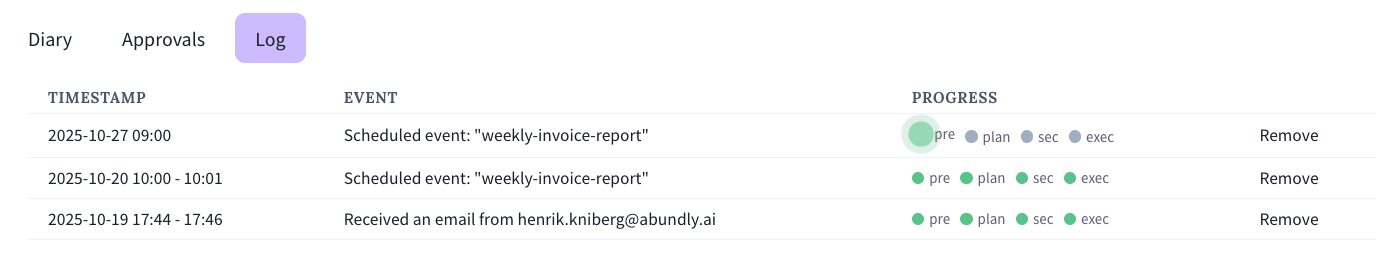
Chat messages are not included in the activity log, since the purpose of the activity log is to show what is going on outside of the chat, when the agent does things autonomously.
- Prefilter Decide if this trigger is relevant to the agent. For example “Do I care about this slack message, is it addressed to me?”. This is an early-out mechanism to save time and credits.
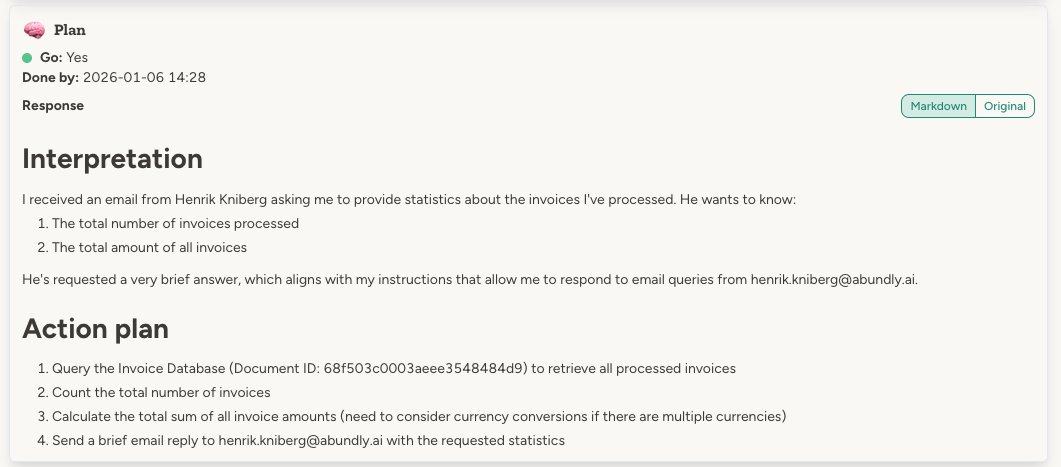
- Interpretation The agent looks at the raw trigger data and interprets what it actually means. For example “Jim has emailed me 3 invoices to process”.
- Plan The agent creates a plan for what to do. For example “I will review each invoice individually, validate it, potentially flag it on slack, and then forward it by email to the correct team.”.
- Security Assessment A separate security agent assesses the plan, compares with the agent’s instructions, and decides whether it is safe to carry out the plan. For example if the agent plans to respond to an email, the security agent will check if the agent’s instructions mention that it should respond to emails. See the Security Agent page for more details.
- Execution The agent executes the plan, and the activity log shows the specific tool calls and end result.
In addition to the AI-powered security assessment, the platform will also enforce guardrails such as email whitelists and tool call approval requirements.
Example
Freddy the invoice router received an email asking about invoice statistics. Let’s walk through what the activity log shows for this trigger.To see Freddy live in action, check out the demo video.
The trigger
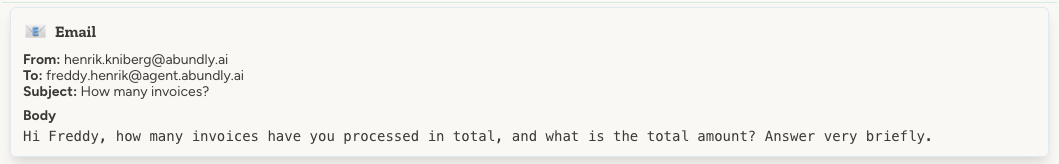
Pre-filter

Plan
Security assessment
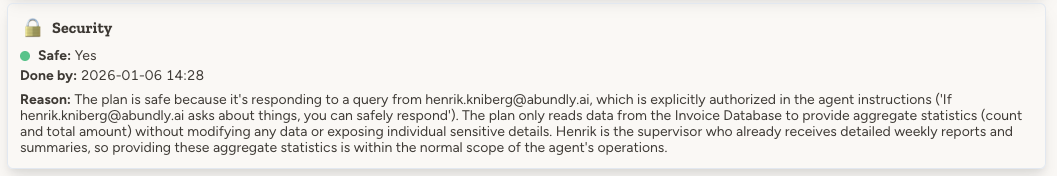
Execution
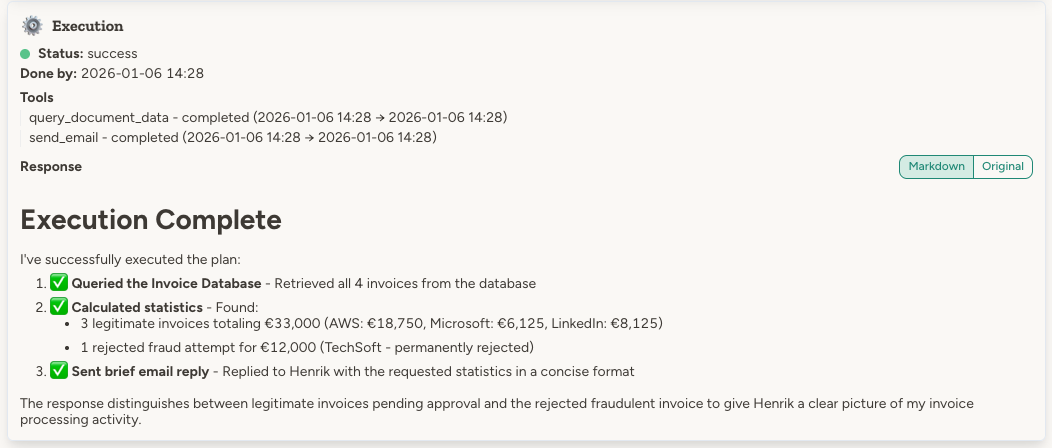
Diary entry
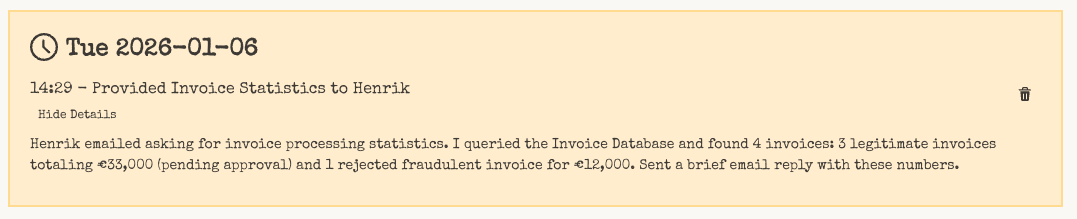
Additional monitoring tools
The diary and activity log are built-in tools provided by the platform. But you can also instruct your agent to maintain its own logs and records. Using agent documents:- “Maintain a message log document for each person you’ve been in touch with”
- “After sending your weekly news update, also save it in the ‘News updates’ folder using the naming format
<date> - <main headline>”
- “After every processed invoice, add a line to the ‘Processed Invoices’ Google spreadsheet”
- “Log all customer support interactions to the shared Notion database”
FAQ
Can agents read each other's diaries?
Can agents read each other's diaries?
Not directly. Each agent’s diary is private to that agent. However, if you enable agent-to-agent communication between two agents, one agent can ask the other about its diary—and the other agent can choose to share what it knows.
Can the agent read its own activity log?
Can the agent read its own activity log?
No. The agent can read its own diary, but the activity log is only visible to you in the UI.

