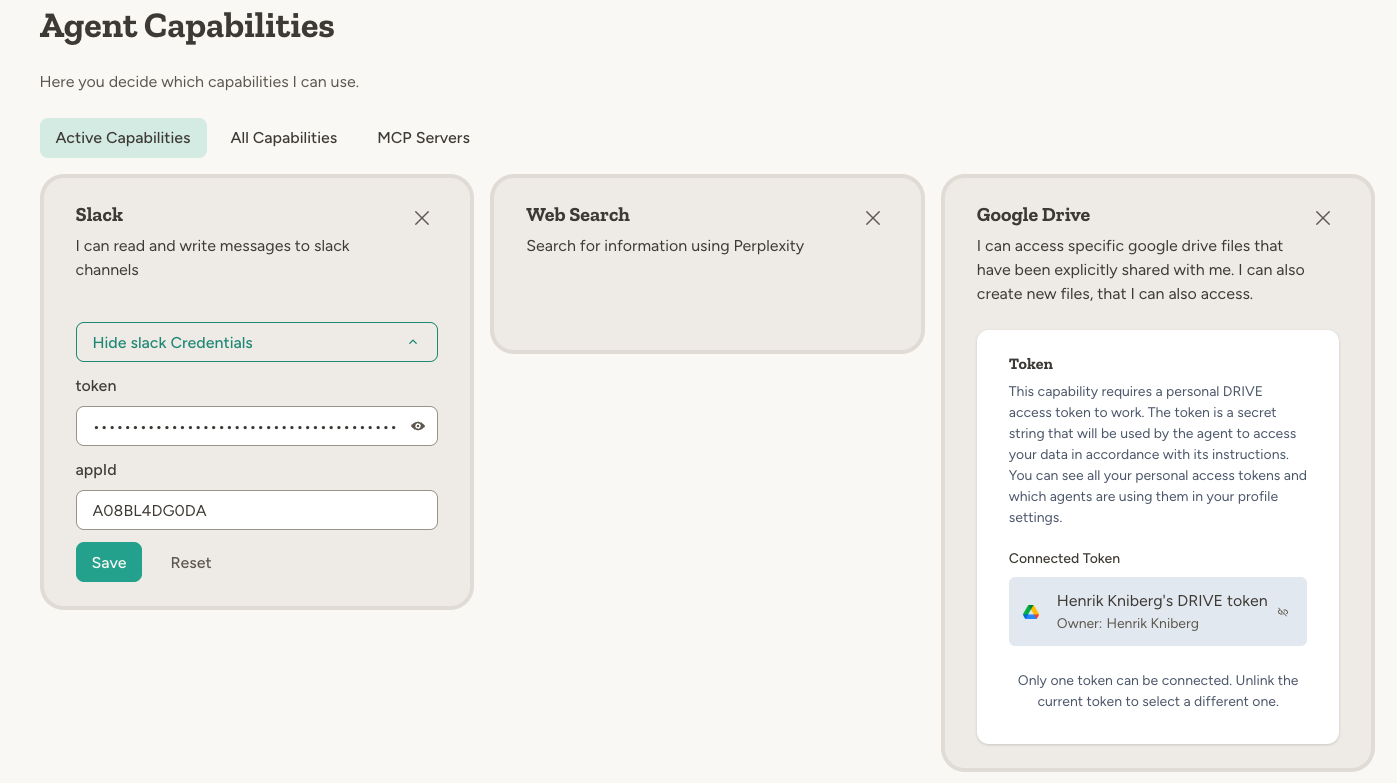
Three credential patterns
Platform-provided
Some capabilities work out of the box with no credentials required. The platform uses its own accounts and you pay through credits. Example: Web Search uses Perplexity under the hood. You just enable the capability and start using it—credits are deducted for usage.User-entered credentials
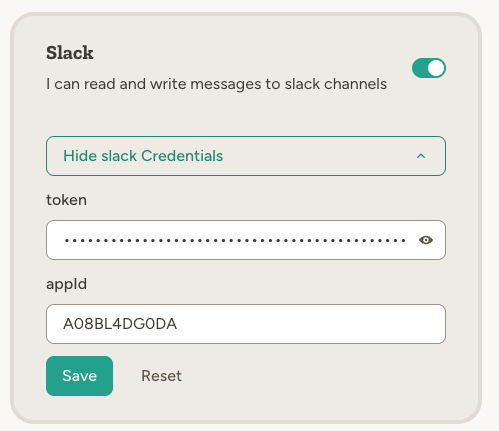
For services where you bring your own account, you enter credentials directly in the capability settings. Typically this means pasting an API token or key. Example: Slack requires a bot token and app ID from your Slack workspace. You create a Slack app, copy the credentials, and paste them into the capability settings.Personal tokens (OAuth)
For services that access your personal data, you authorize via OAuth. This creates a personal token tied to your account. Example: Google Drive requires access to your Google account. You click “Connect” and authorize through Google’s OAuth flow. The resulting token is yours—other users who interact with the agent can trigger actions, but only within the scope you authorized.Managing personal tokens
Personal tokens are managed in your profile settings under Personal Tokens. You can see all your connected services, add new tokens, and revoke access.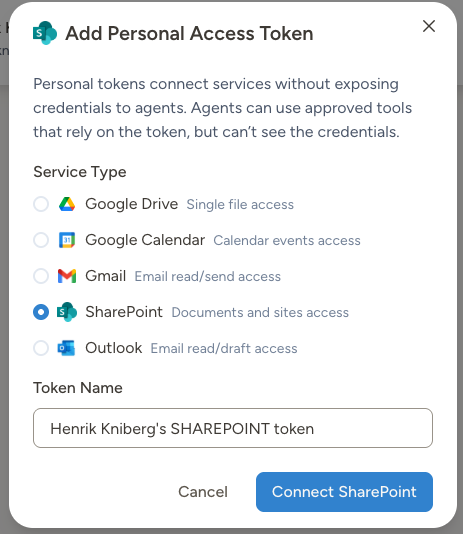
- Google Drive
- Google Calendar
- Gmail
- SharePoint
- Outlook
How credentials are secured
| Measure | Description |
|---|---|
| Encrypted storage | Stored encrypted in database—not readable even with database access |
| Key separation | Decryption keys stored separately from encrypted data |
| Access control | Only authorized agents can use specific credentials |
| No LLM exposure | Credentials are never included in prompts or visible to the LLM |
| Auto-refresh | OAuth tokens are automatically refreshed before they expire |
The LLM never sees your credentials. It only knows which capabilities are available (e.g., “Gmail - Read and send emails”). When an agent calls an external API, the platform injects authentication after the LLM has generated the request. This prevents credentials from leaking through model outputs or logs.
Best practices
Use least privilege. When creating API keys or OAuth grants, give only the permissions the agent actually needs. A read-only key is safer than one with write access. Rotate after team changes. When someone leaves your team, rotate any credentials they might have had access to through agents. Revoke unused tokens. In your Personal Tokens page, remove tokens for services you no longer use. Never put credentials in instructions. Credentials in agent instructions would be visible to anyone with access to the agent and potentially exposed in logs. Always use the credential system.If a credential is compromised
If you suspect a credential has been compromised:- Revoke immediately — For personal tokens, go to your Personal Tokens page and disconnect the service. For user-entered credentials, regenerate the API key at the source (e.g., Slack, GitHub).
- Update agents — Any agents using that credential will lose access until you reconnect with new credentials.
- Review activity — Check the activity log for any suspicious actions taken before the credential was revoked.

