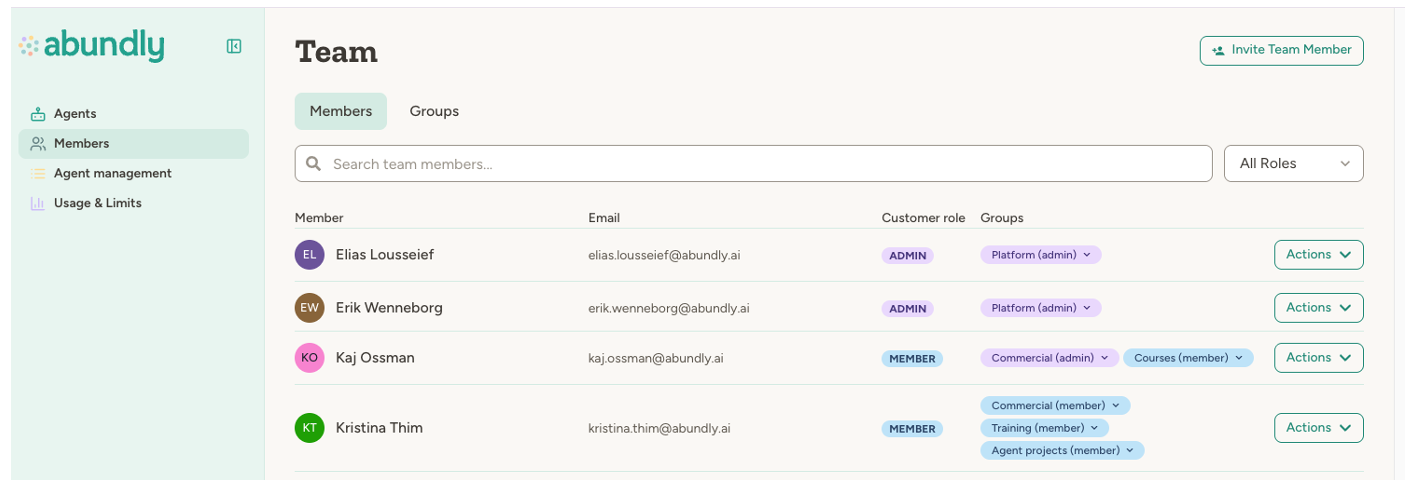
Organization roles
Every user in your organization has a role that determines their base level of access:| Role | Description |
|---|---|
| Admin | Full control over the organization—can manage members, billing, capabilities, and all agents |
| Member | Standard team member—can access agents based on agent-level settings |
| Guest | Limited access—can only access agents they’ve been explicitly granted access to |
Agent access levels
Each agent has access settings that control what team members can do with it. There are four levels:| Level | What it allows |
|---|---|
| Admin | Full control: delete agent, change access settings, edit configuration, interact |
| Edit | Modify instructions, capabilities, documents, and interact with the agent |
| Use | Interact with the agent (chat), but cannot change anything |
| None | Cannot see or interact with the agent |
Team access vs. user-specific access
Agent access is controlled through two settings, found in the agent’s Settings > Team access tab: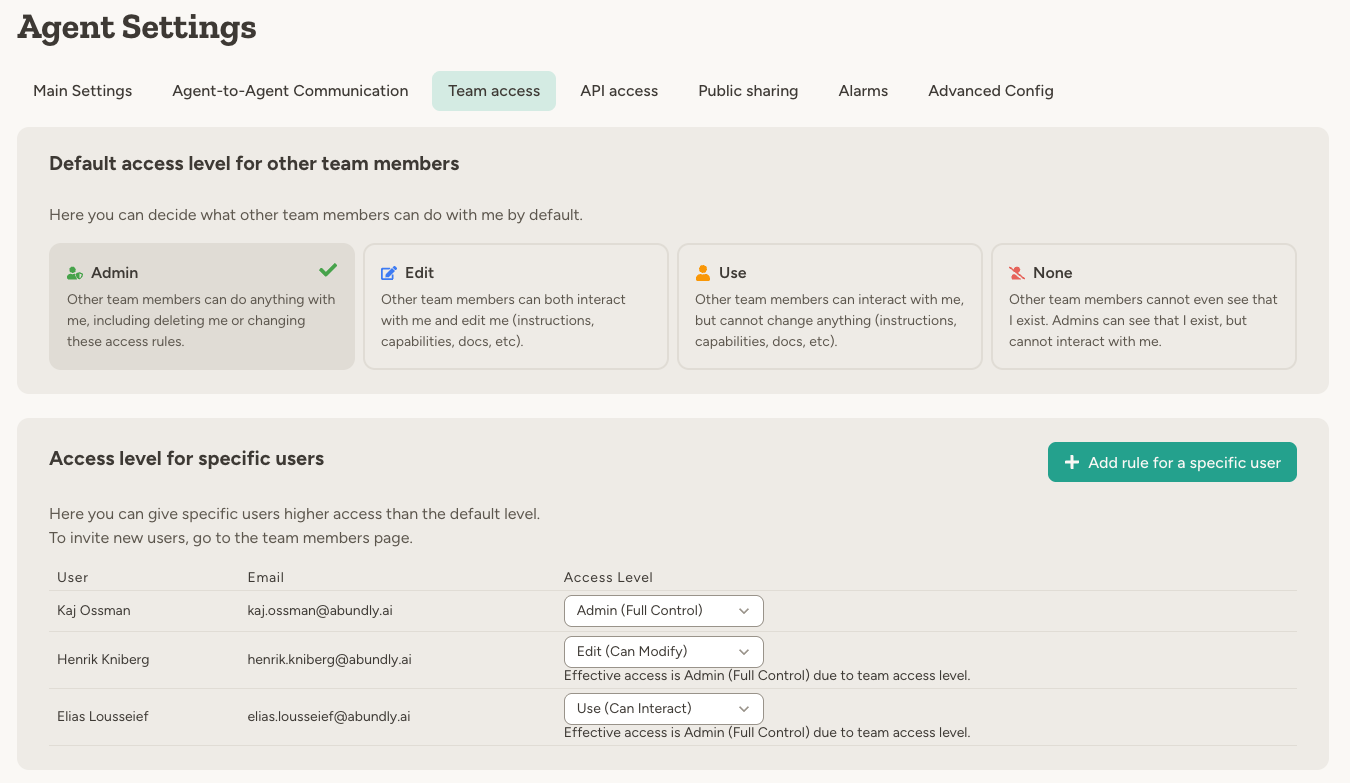
The system always grants the highest access level between team access and user-specific access. User-specific rules are typically used to grant more access, not less.
Private agents
When you set team access to “None,” the agent becomes private:- Regular team members cannot see the agent—it won’t appear in their agent list
- Organization administrators can still see it exists (for administrative purposes)
- Only users with explicit user-specific access can interact with it
Groups
For larger organizations, groups add another layer of access control between organization and agent:- Agents can belong to a group
- Users must be members of that group to access the agent (unless they’re organization admins)
- Group admins can manage agents within their group
Groups are an enterprise feature. Contact support@abundly.ai to enable them for your organization.
Agent-to-agent access
Control which agents can communicate with each other. This is configured in each agent’s settings under “Agent-to-Agent Communication.”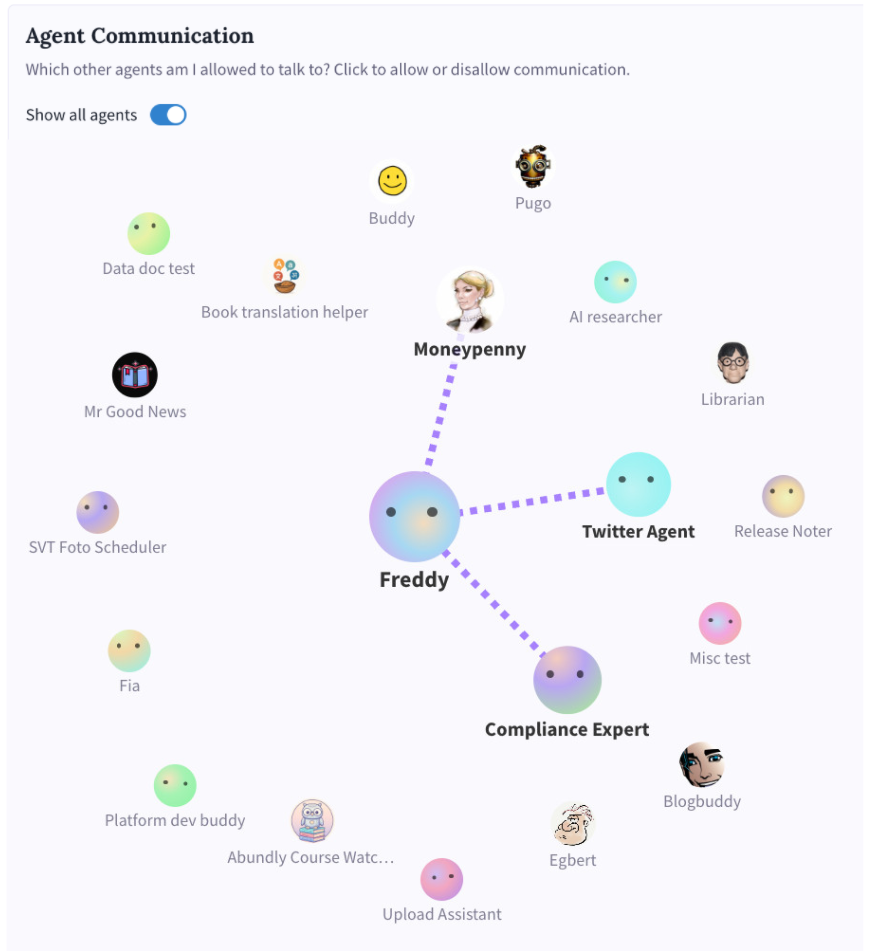
Best practices
Start with restrictive defaults. Set team access to “Use” or “None” for sensitive agents, then grant higher access to specific users who need it. Use groups for scale. If you have many agents or multiple teams, groups make access management much simpler than per-agent user rules. Review access after team changes. When someone leaves or changes roles, audit their access to ensure it’s still appropriate. Keep at least one admin. The platform prevents you from removing all admin access from an agent—every agent needs at least one administrator.FAQ
What's the difference between 'Edit' and 'Admin' access?
What's the difference between 'Edit' and 'Admin' access?
Edit access lets you modify how the agent works—instructions, capabilities, documents, and other settings.Admin access includes everything in Edit, plus the ability to delete the agent and change who else can access it.
Can I restrict a user to less access than the team default?
Can I restrict a user to less access than the team default?
No. The system always grants the highest access level between team access and user-specific access. If you need to restrict specific users, set the team default to a lower level (like “None”), then grant higher access to the users who should have it.
Can Guests use agents?
Can Guests use agents?
Guests cannot access agents through team access—they need explicit user-specific access to each agent. This makes the Guest role useful for external collaborators who should only see specific agents.
Do I need to be in a group to access an agent in that group?
Do I need to be in a group to access an agent in that group?
Yes. If an agent belongs to a group, you must be a member of that group to access it. The exception is organization administrators, who automatically have access to all groups.
Can agents access each other's data?
Can agents access each other's data?
Only if you explicitly configure agent-to-agent communication between them. By default, agents are isolated—they can’t see each other’s documents, databases, or conversations.
What happens when someone leaves the organization?
What happens when someone leaves the organization?
Remove them from the organization in the Members page. They’ll immediately lose access to all agents and data. Their past conversations and actions remain in the logs.

